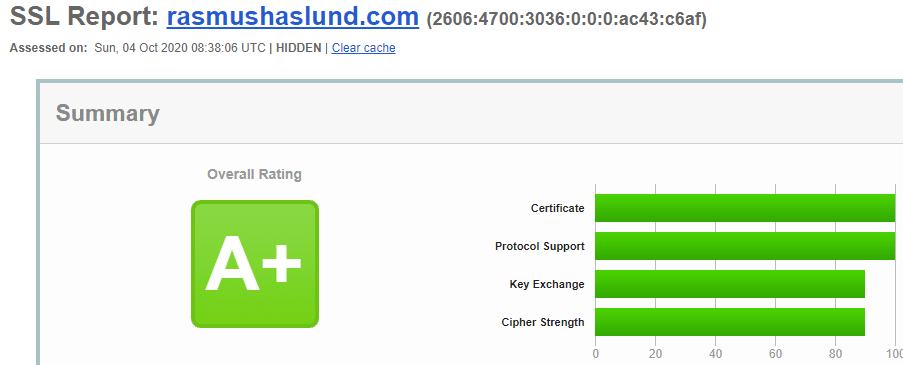
Preface: I implemented SSL for the blog originally back in 2015, if you are wondering how you can get SSL up and running and with a good SSL Labs score check out this post.
I recently ran the Qualys SSL Labs report against my new domain rasmushaslund.com and received an overall score of B
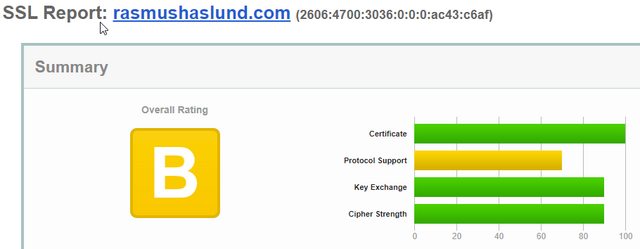
A few issues presented:
- This server supports TLS 1.0 and TLS 1.1. Grade capped to B
- DNS CAA: No
- Weak ciphers used (although AES128 and in some cases even AES256)
- HTTP Strict Transport Security (HSTS): No
- HSTS Preloading Not in: Chrome Edge Firefox IE
- 0-RTT enabled: No
Disable TLS 1.0 and TLS 1.1
I am using the free plan of cloudflare.com and fortunately, this makes it very easy to disable TLS 1.0 and TLS 1.1. Simply navigate to the SSL/TLS section and select the Edge Certificates to adjust the Minimum TLS Version setting:
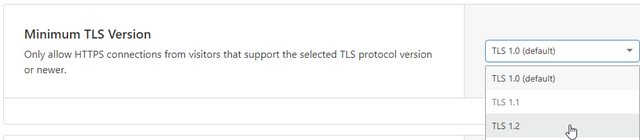
This one change bumped the score from B to A.
Implement DNS CAA records
Certification Authority Authorization (CAA) is a standard to basically restrict which Certificate Authorities (CA) can issue certificates for a domain name. This means we need to add a CAA record to our DNS records to be compliant. I am using Cloudflare and their Universal SSL system which means certificates could be issued automatically by multiple CAs. Fortunately, Cloudflare lists even which CAA records to set up in their FAQ. You can read more about CAA records here.
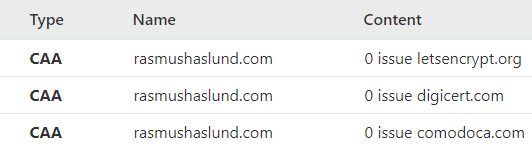
There score remained at A.
Weak ciphers used
The test stated the following ciphers are weak:
- TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA
- TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA256
- TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA
- TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA384
The different ciphers can be looked up using the CipherSuite website. Unfortunately, I can’t really do much about this as a free user of Cloudflare. I would need to either pay $10 USD/month for their Advanced Certificates or upgrade to their $200 USD/month business plan.
HTTP Strict Transport Security (HSTS)
HTTP Strict Transport Security (HSTS) is a security policy to protect websites against man in the middle attacks and cookie hijacking. Basically, the server will tell the web browser to only connect using HTTPS securely.
I added the following line to my .htaccess file:
Header set Strict-Transport-Security “max-age=63072000; includeSubDomains; preload”
Another SSL Labs scan showed the score increased now from A to A+.
HSTS Preloading Not in: Chrome Edge Firefox IE
HSTS preloading means your browser has a list of websites that it will NEVER connect to using HTTP and instead ONLY connect to using HTTPS. Once a website has been correctly set up, it can be requested for inclusion on the Chrome HSTS preload list on this form. The list is also used by Firefox, Opera, and most other browsers.
Notice it can take a while to be included on the preload list. Mine was included after about a week.
0-RTT
Basically, this feature improves performance for users who have previously connected to the site. For example, someone is opening a new link on the site. Cloudflare has a good in-depth article. This article explains some security concerns well, but note that Cloudflare has mitigated the concerns.
I saw articles mention Cloudflare enables this by default on their free plan, but this no longer seems to be the case at least. To enable it, navigate on Cloudflare to Network and enable the 0-RTT Connection Resumption feature.
Final report